Hello everyone, in this tutorial I’ll discuss about how to configuration DNAT or Destination NAT on fortigate using a virtual IP. Scenario that will be used in this tutorial is we want to make some Routers/Servers behind the fortigate in DMZ Zone can be access through a Virtual IP from WAN Zone so that routers/servers is’t no need to directly pointing on public ip or wan section.
Here’s the topology used :
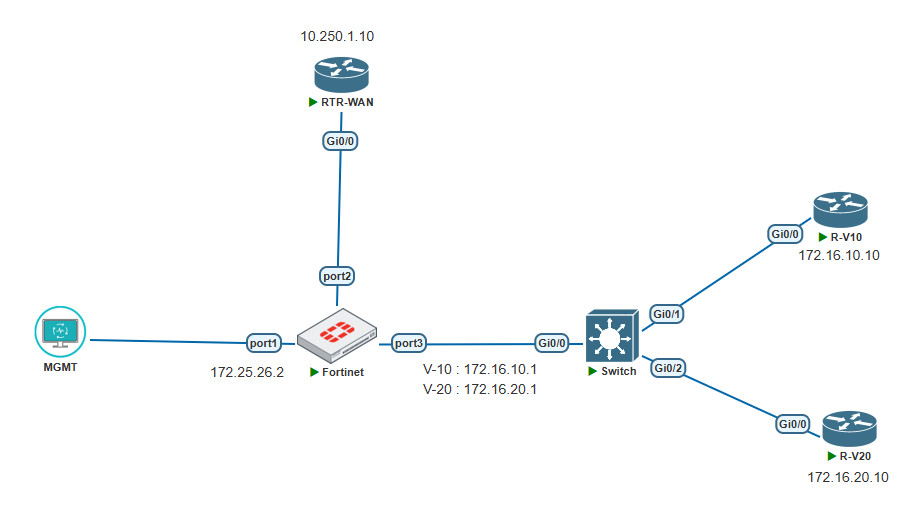
Here’s the simulation concept :
- When from RTR-WAN access to ip 10.0.0.1 it will be redirect to 172.16.10.10 (R-V10)
- When from RTR-WAN access to ip 10.0.0.2 it will be redirect to 172.16.20.10 (R-V20)
First Configure IP Address for RTR-WAN
RTR-WAN(config)# interface GigabitEthernet0/0 RTR-WAN(config-if)# ip address 10.250.1.2 255.255.255.0
On RTR-WAN configure ip route for 10.0.0.0/24 network to fortigate ip 10.250.1.1
RTR-WAN# ip route 10.0.0.0 255.255.255.0 10.250.1.1
Configure VLAN & Config Port on Switch
Switch(config)#vlan 10 Switch(config-vlan)#exit Switch(config)#vlan 20 Switch(config-vlan)#exit Switch(config)#
Configure interface trunk through fortigate firewall :
Switch(config)#int g0/0 Switch(config-if)#switchport trunk encapsulation dot1q Switch(config-if)#switchport mode trunk Switch(config-if)#exit
Configure interface vlan access through R-V10 & R-V20
Switch(config)#int g0/1 Switch(config-if)#switchport mode access Switch(config-if)#switchport access vlan 10 Switch(config-if)#exit Switch(config)#int g0/2 Switch(config-if)#switchport mode access Switch(config-if)#switchport access vlan 20 Switch(config-if)#exit
Configure IP Address & Default gateway on R-V10
interface GigabitEthernet0/0 ip address 172.16.10.10 255.255.255.0ip route 0.0.0.0 0.0.0.0 172.16.10.1
Configure IP Address & Default gateway on R-V20
interface GigabitEthernet0/0 ip address 172.16.20.10 255.255.255.0ip route 0.0.0.0 0.0.0.0 172.16.20.1
Now Let’s configure the Fortigate Firewall. If you need to do a basic configuration fortigate, Please refers these link : Basic Configuration Fortigate Firewall
Configure the port3 as DMZ role, then create 2 VLAN interfaces and configure each IP Addresses .
Port2 is MGMT port which is for management access usage so we can access through the laptop to fortigate VM on PNETLAB.
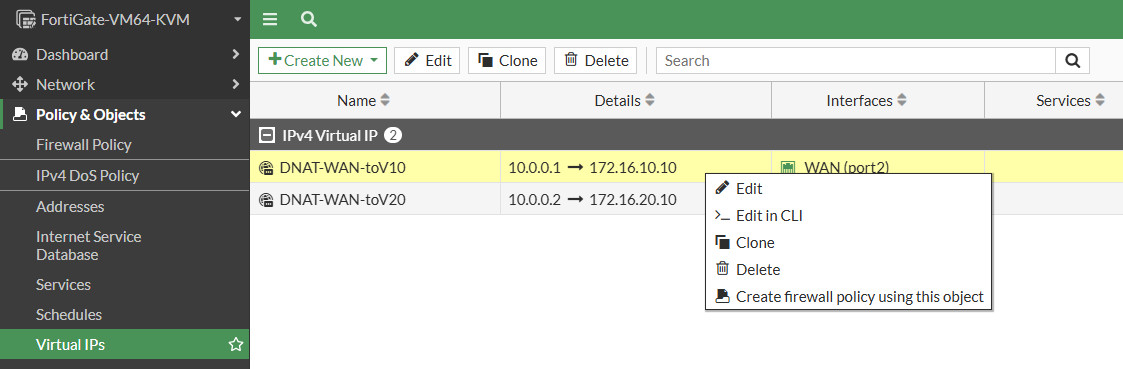
Configure Virtual IPs > Select Create New > Virtual IP

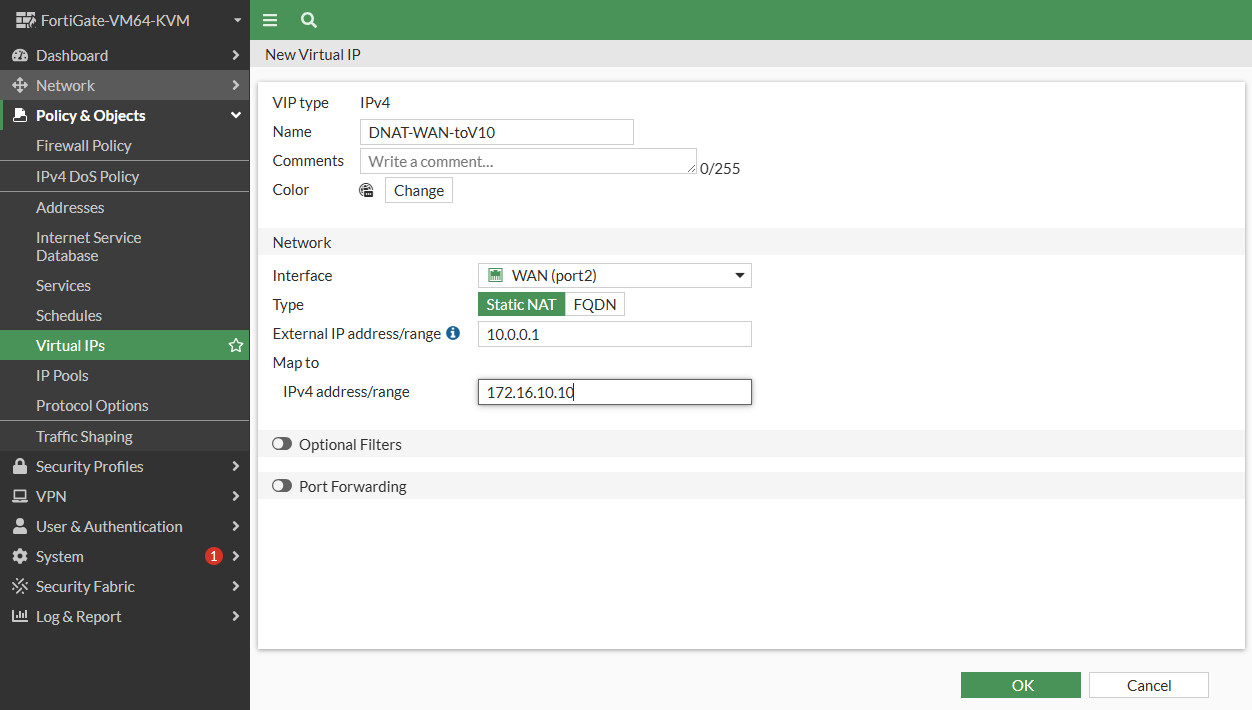
Create new virtual IP for DNAT WAN to Router VLAN 10, Select interface for WAN access, external IP is the ip that used for virtual ip and Map to is used for redirect on local ip address or ip address under the fortigate firewall (DMZ).
Do the same way for DNAT WAN to Router Vlan 20.
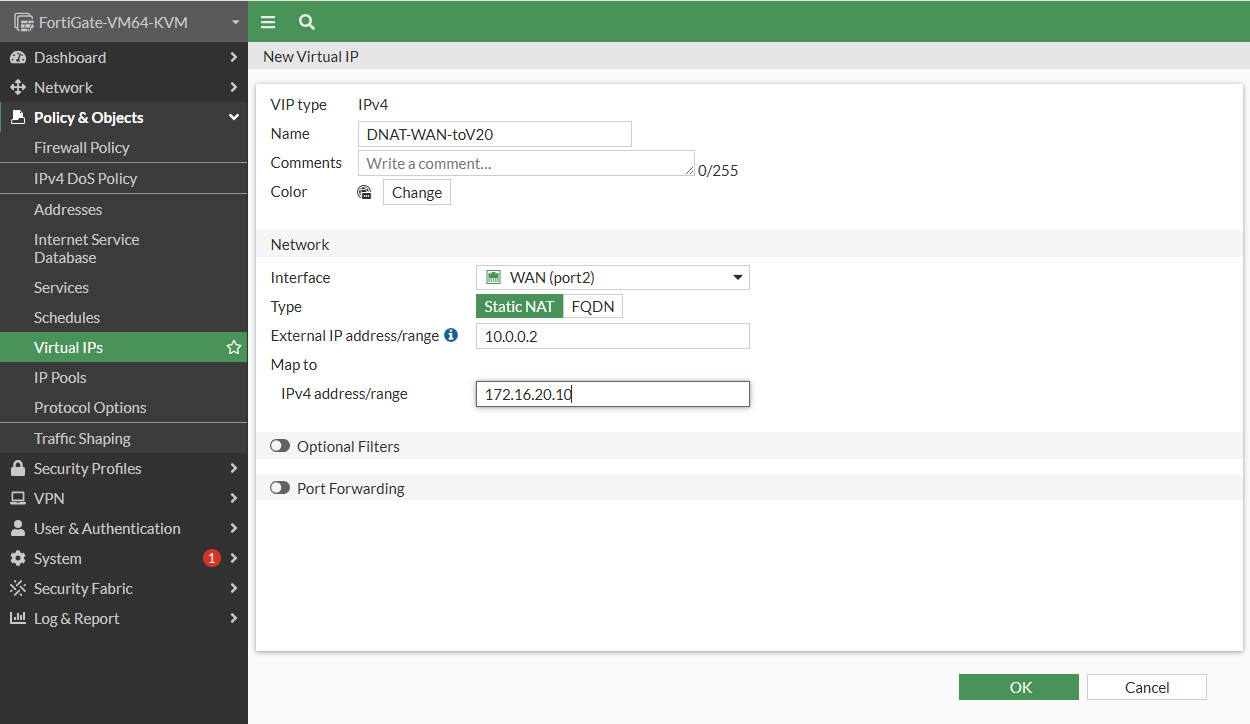
After you have to create 2 Virtual IPs, Create the firewall policy for the 2 these virtual IPs. Right click on Virtual IPs then select Create firewall policy using this object.
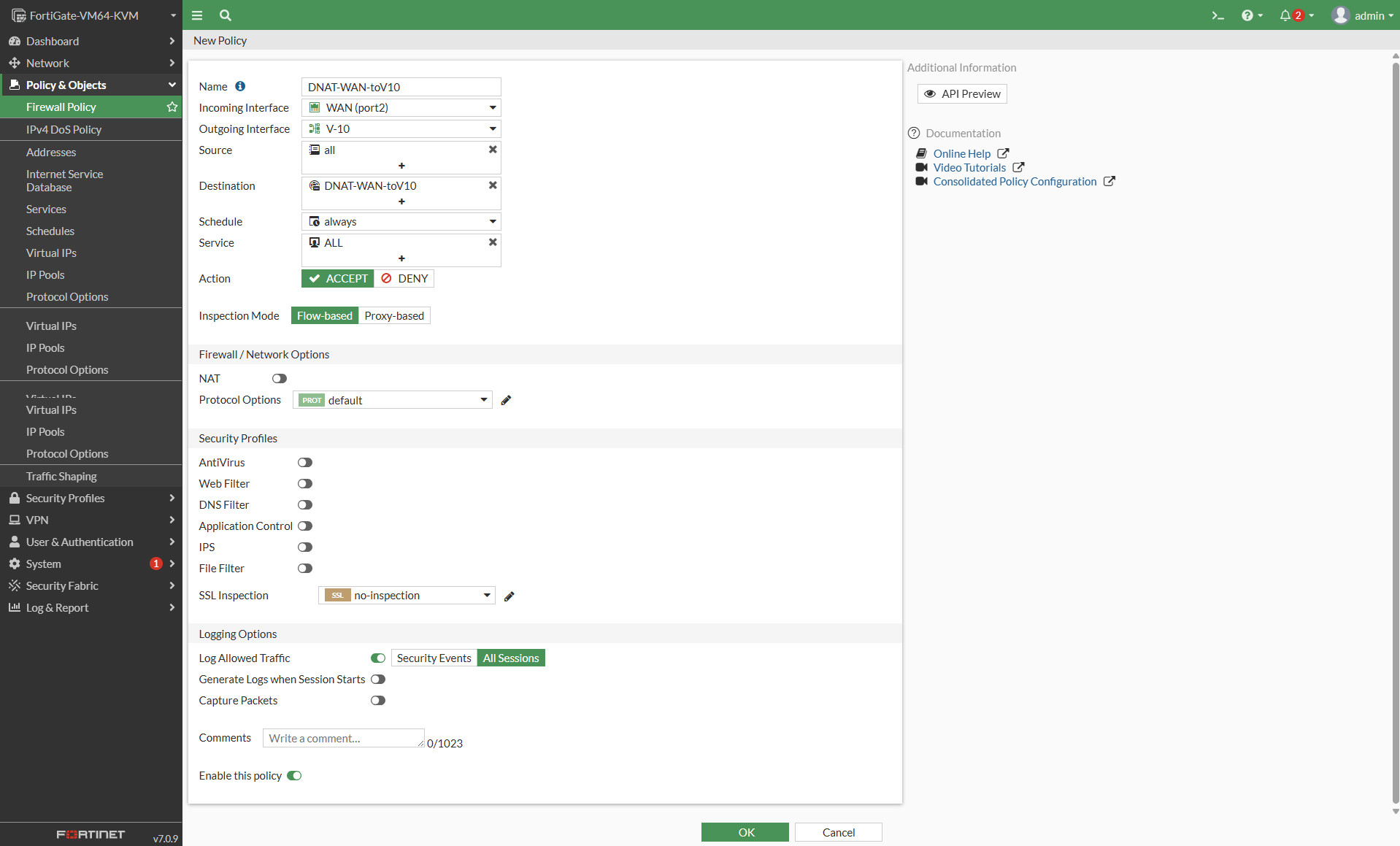
Firewall Policy for DNAT-WAN-toV10
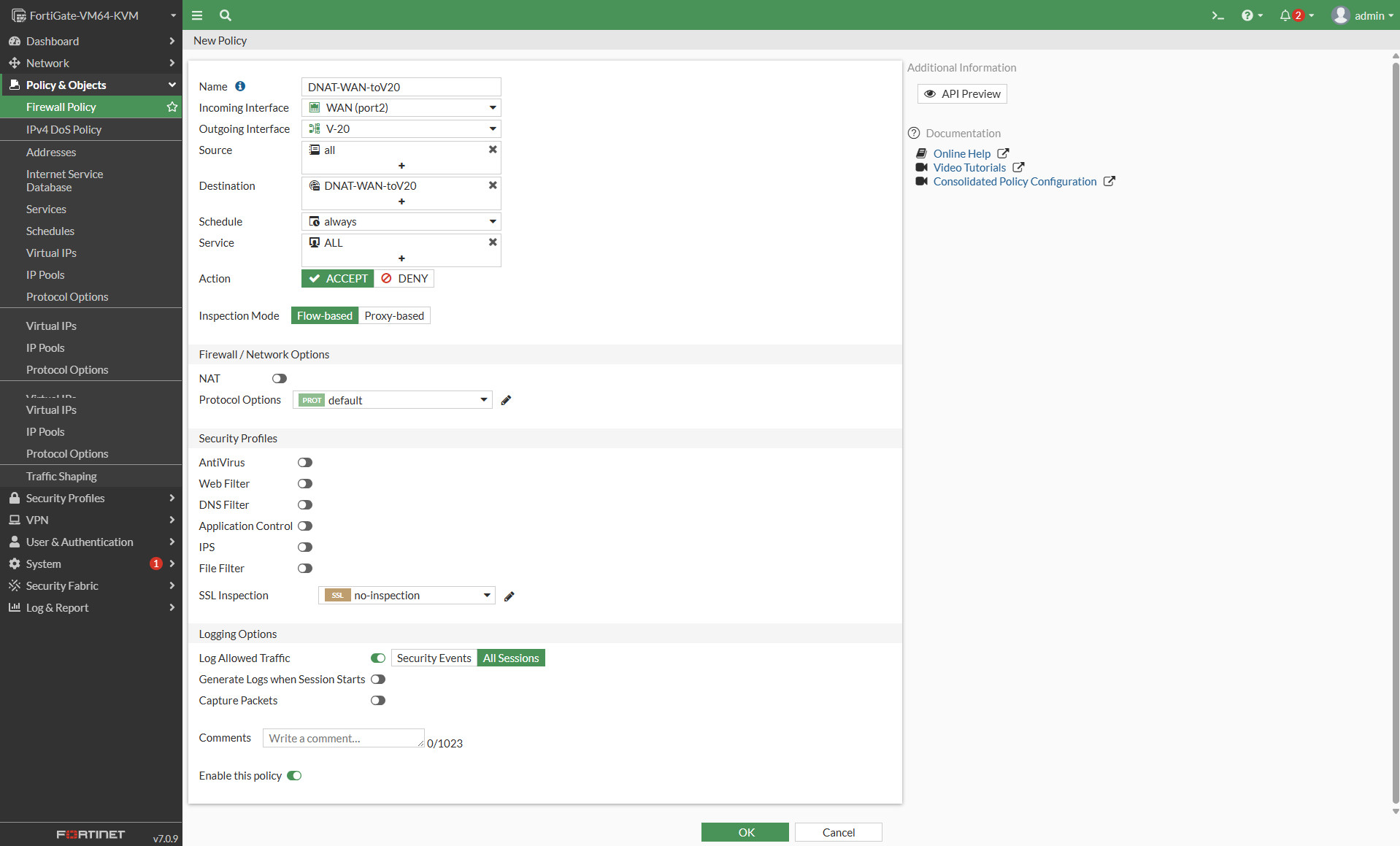
Firewall Policy for DNAT-WAN-toV20
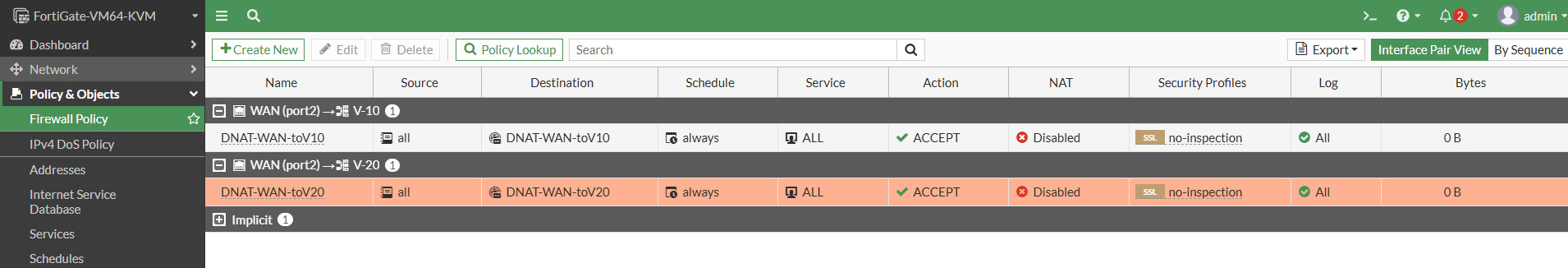
Now test the configuration :
Activate debug ip icmp on R-V10 and R-V20
R-V10#debug ip icmp ICMP packet debugging is on R-V10#R-V20#debug ip icmp ICMP packet debugging is on R-V20#
- Do a ping test from RTR-WAN
RTR-WAN#ping 10.0.0.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.0.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/11/24 ms RTR-WAN#
Then look at the debug log on R-V10. as shown bellow, you can see echo replay from 172.16.10.10 (ip address V-10) is send to 10.250.1.2 (ip address of RTR-WAN).
R-V10# *Jul 22 13:46:20.441: ICMP: echo reply sent, src 172.16.10.10, dst 10.250.1.2, topology BASE, dscp 0 topoid 0 *Jul 22 13:46:20.455: ICMP: echo reply sent, src 172.16.10.10, dst 10.250.1.2, topology BASE, dscp 0 topoid 0 *Jul 22 13:46:20.467: ICMP: echo reply sent, src 172.16.10.10, dst 10.250.1.2, topology BASE, dscp 0 topoid 0 *Jul 22 13:46:20.476: ICMP: echo reply sent, src 172.16.10.10, dst 10.250.1.2, topology BASE, dscp 0 topoid 0 *Jul 22 13:46:20.482: ICMP: echo reply sent, src 172.16.10.10, dst 10.250.1.2, topology BASE, dscp 0 topoid 0 R-V10#
From the test above is indicated the configuration was successfull. so when the RTR-WAN try ping connection to ip 10.0.0.1, then fortigate will be redirect the connection to 172.16.10.10 which it’s the router at DMZ.
2. Also test for the 10.0.0.2 ip
RTR-WAN#ping 10.0.0.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 5/8/23 ms RTR-WAN#
The connection test is also successfull. when the RTR-WAN try ping connection to ip 10.0.0.2 it will redirect to the 172.16.20.10
R-V20# *Jul 22 14:02:44.928: ICMP: echo reply sent, src 172.16.20.10, dst 10.250.1.2, topology BASE, dscp 0 topoid 0 *Jul 22 14:02:44.937: ICMP: echo reply sent, src 172.16.20.10, dst 10.250.1.2, topology BASE, dscp 0 topoid 0 *Jul 22 14:02:44.943: ICMP: echo reply sent, src 172.16.20.10, dst 10.250.1.2, topology BASE, dscp 0 topoid 0 *Jul 22 14:02:44.949: ICMP: echo reply sent, src 172.16.20.10, dst 10.250.1.2, topology BASE, dscp 0 topoid 0 *Jul 22 14:02:44.956: ICMP: echo reply sent, src 172.16.20.10, dst 10.250.1.2, topology BASE, dscp 0 topoid 0 R-V20#