Hello everyone, In this tutorial I’ll discuss about how to restrict an SSH Access only for specific network segment so only specific ip or network that can be access the switch or router.
Here’s the topology used :
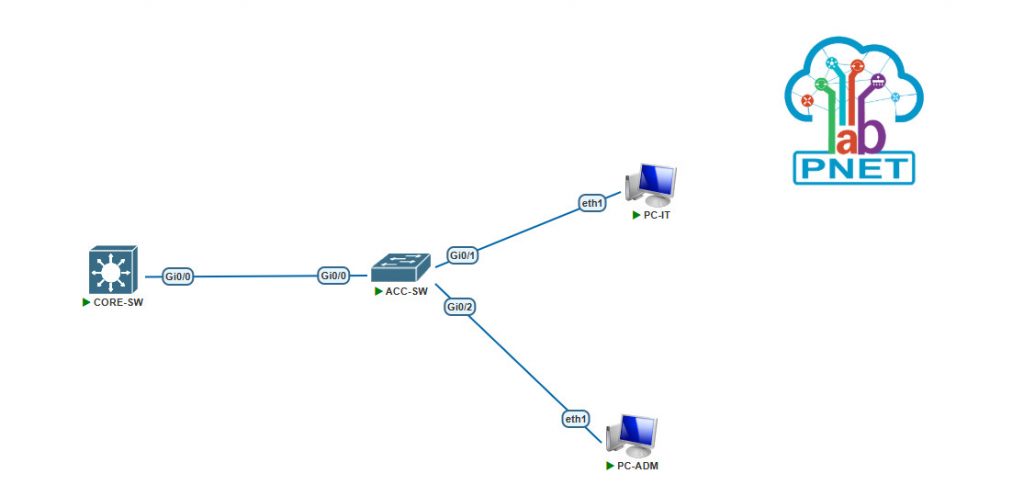
Scope of configuration :
- Basic Config
- DHCP Server https://www.taufiknurhuda.web.id/2022/07/06/how-to-configuration-dhcp-server-on-router-cisco/
- SSH Configuration
- Access List
- Restrict Remote Access
Network Configuration :
- VLAN 10 [Management] – 10.250.1.0/24
- VLAN 20 [IT] – 172.16.100.0/24
- VLAN 30 [Admin] – 172.16.200.0/24
Configure VLAN Interface, IP Address & Trunk interface on CORE Switch
CORE-SW(config)#vlan 10 CORE-SW(config-vlan)#name Management CORE-SW(config-vlan)#exit CORE-SW(config)#vlan 20 CORE-SW(config-vlan)#name IT CORE-SW(config-vlan)#exit CORE-SW(config)#vlan 30 CORE-SW(config-vlan)#name ADMIN CORE-SW(config-vlan)#exitCORE-SW(config)#int vlan 10 CORE-SW(config-if)#no shut CORE-SW(config-if)#ip add 10.250.1.1 255.255.255.0 CORE-SW(config-if)#exit CORE-SW(config)#int vlan 20 CORE-SW(config-if)#ip add 172.16.100.1 255.255.255.0 CORE-SW(config-if)#no shut CORE-SW(config-if)#exit CORE-SW(config)#int vlan 30 CORE-SW(config-if)#ip add 172.16.200.1 255.255.255.0 CORE-SW(config-if)#no shut CORE-SW(config-if)#exit
CORE-SW(config)#int g0/0 CORE-SW(config-if)#switchport trunk encapsulation dot1q CORE-SW(config-if)#switchport mode trunk
Configure DHCP Server on CORE Switch
CORE-SW(config)#ip dhcp excluded-address 10.250.1.1 CORE-SW(config)#ip dhcp excluded-address 172.16.100.1 CORE-SW(config)#ip dhcp excluded-address 172.16.200.1 CORE-SW(config)#ip dhcp pool POOL-IT CORE-SW(dhcp-config)#network 172.16.100.0 255.255.255.0 CORE-SW(dhcp-config)#default-router 172.16.100.1 CORE-SW(dhcp-config)#exit CORE-SW(config)#ip dhcp pool POOL-ADM CORE-SW(dhcp-config)#network 172.16.200.0 255.255.255.0 CORE-SW(dhcp-config)#default-router 172.16.200.1 CORE-SW(dhcp-config)#exit
Configure VLAN & SVI on ACC-SW
ACC-SW(config)#vlan 10 ACC-SW(config-vlan)#name Management ACC-SW(config-vlan)#exit ACC-SW(config)#vlan 20 ACC-SW(config-vlan)#name IT ACC-SW(config-vlan)#exit ACC-SW(config)#vlan 30 ACC-SW(config-vlan)#name ADMIN ACC-SW(config-vlan)#exitACC-SW(config)#int vlan 10 ACC-SW(config-if)#ip add 10.250.1.2 255.255.255.0 ACC-SW(config-if)#no shut ACC-SW(config-if)#exit
Configure Interface Trunk port on ACC-SW
ACC-SW(config)#int g0/0 ACC-SW(config-if)#switchport trunk encapsulation dot1q ACC-SW(config-if)#switchport mode trunk ACC-SW(config-if)#exit
Configure access port. G0/1 for PC-IT and G0/1 for PC-ADM
ACC-SW(config)#int g0/1 ACC-SW(config-if)#switchport mode access ACC-SW(config-if)#switchport access vlan 20 ACC-SW(config-if)#exit ACC-SW(config)#int g0/2 ACC-SW(config-if)#switchport mode access ACC-SW(config-if)#switchport access vlan 30 ACC-SW(config-if)#exit
After that check and makesure the PCs already got the connection.
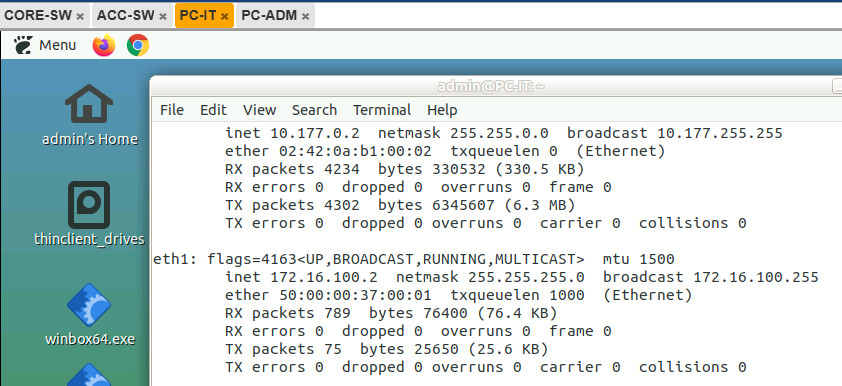
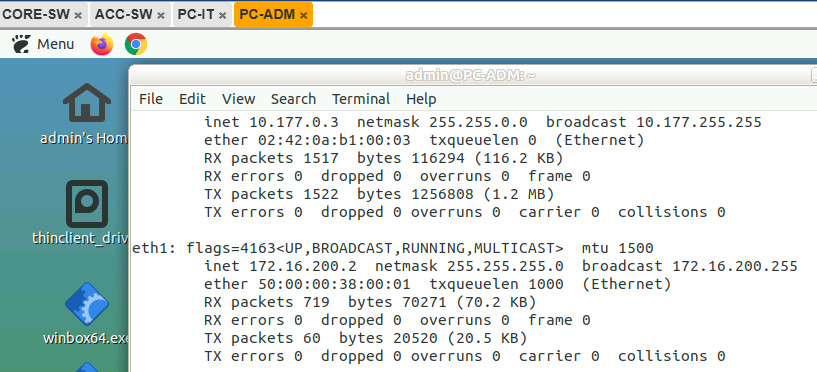
Configure SSH on CORE switch for general/basic remote connection.
CORE-SW(config)#ip domain-name taufiknurhuda.web.id CORE-SW(config)#crypto key gen rsa mod 2048 The name for the keys will be: CORE-SW.taufiknurhuda.web.id % The key modulus size is 2048 bits % Generating 2048 bit RSA keys, keys will be non-exportable... [OK] (elapsed time was 0 seconds) CORE-SW(config)# *Jul 19 16:32:00.635: %SSH-5-ENABLED: SSH 1.99 has been enabled CORE-SW(config)#ip ssh version 2
Configure username for login access & configure line vty
CORE-SW(config)#username taufik privilege 15 secret mysecret CORE-SW(config)#line vty 0 15 CORE-SW(config-line)#transport input ssh CORE-SW(config-line)#login local CORE-SW(config-line)#exit
Initial test from both PC, SSH Access is success from PC-IT and PC-ADM
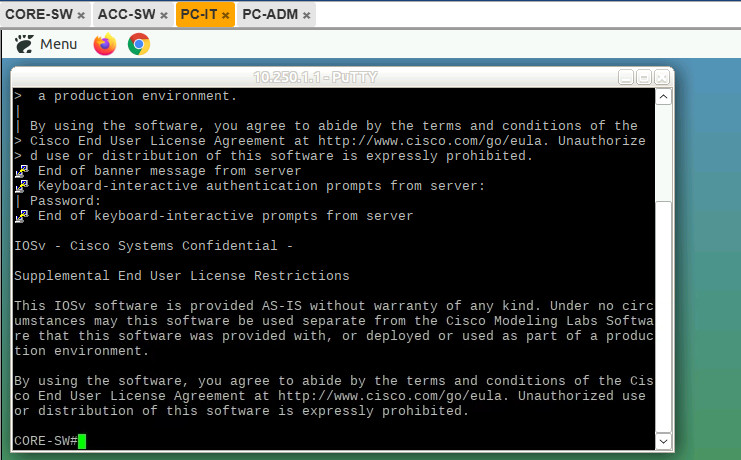
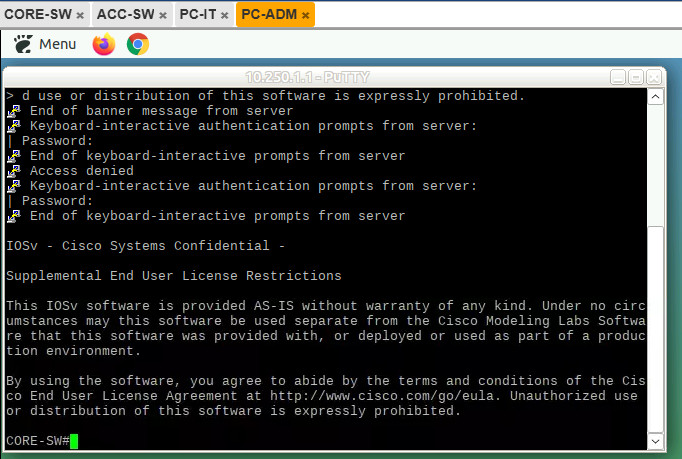
Now is the point of. Set the policy that SSH Access to CORE switch is only allow from IT segment so if user ADMIN try to remote access it doesn’t allow to access.
Configure ACL (Access Control List) to permit IT Segment :
CORE-SW(config)#ip access-list standard PermitSSH CORE-SW(config-std-nacl)#permit 172.16.100.0 0.0.0.255 log CORE-SW(config-std-nacl)#exit
Configure access-class on the line vty :
CORE-SW(config)#line vty 0 15 CORE-SW(config-line)#access CORE-SW(config-line)#access-class PermitSSH in CORE-SW(config-line)#exit
Then do a test again and look at the differents.
PC-IT with segment 172.16.100.0 is allowed to remote access CORE Switch.
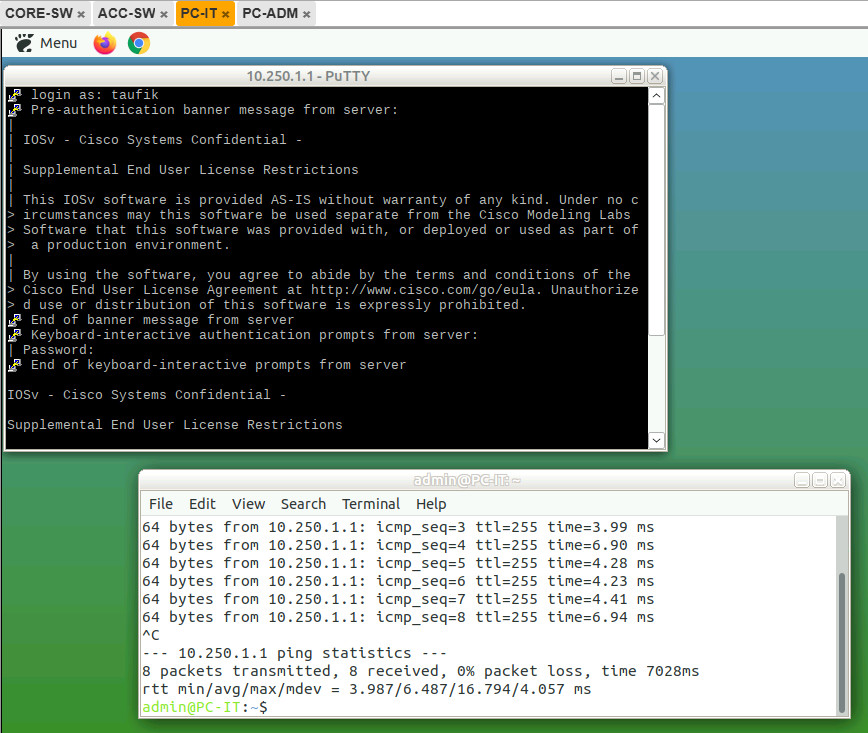
While when PC-ADM try to remote access CORE Switch, the connection is refused. Other connection like ping is still normal / doesn’t blocked.
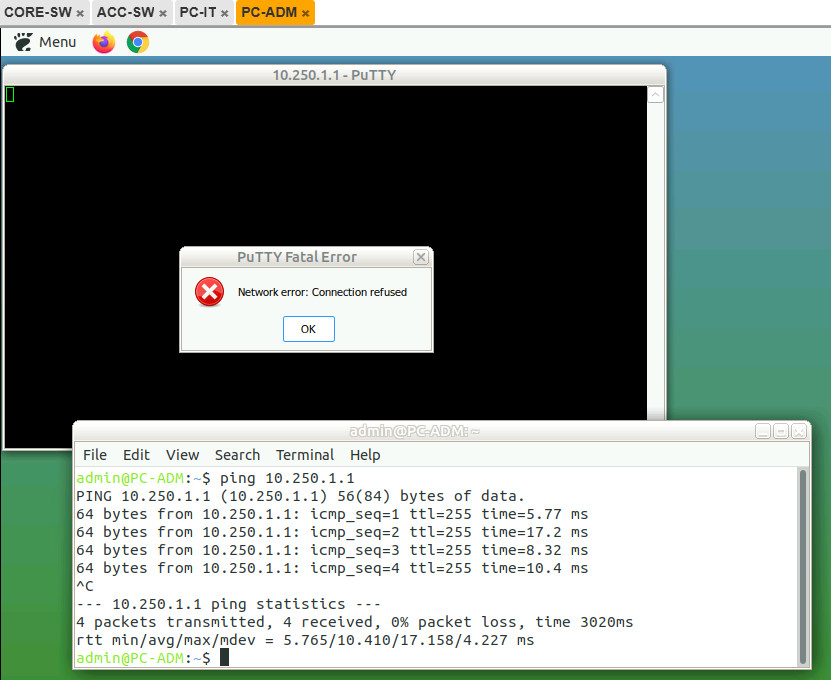
Here’s a Log when PC-IT is success remote to CORE Switch :
CORE-SW# *Jul 19 16:44:24.740: %SEC-6-IPACCESSLOGNP: list PermitSSH permitted 0 172.16.100.2 -> 0.0.0.0, 1 packet CORE-SW#